Abstract
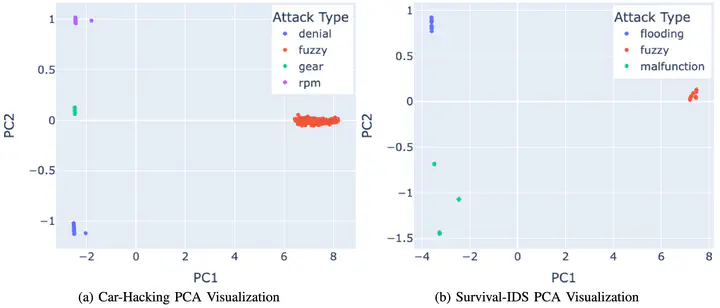
Even though the CAN bus is the industry standard for in-vehicle communication, it is vulnerable to attacks by malicious agents. Existing research has focused on detecting and classifying such attacks; however, there is a gap in identifying novel attack types. Current classification approaches use models trained with knowledge of all possible attack types at training time. This approach does not reflect real-world scenarios, where systems may encounter novel attacks after deployment. In this paper, we propose a methodology to identify the number of different attack types a system has encountered. In our initial experiments, our clustering-based methodology successfully encounters cluster assignments that match attack types in the data. Furthermore, it identifies novel attack types with as little as one data point and an average of less than five data points, showing the promise of this framework to enable on-vehicle continual learning.