 LOCoCAT Framework Overview
LOCoCAT Framework Overview
Abstract
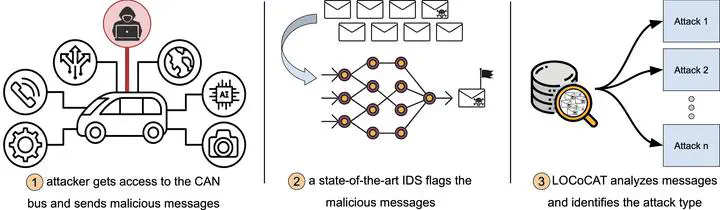
Although research has shown vulnerabilities and shortcomings of the controller area network bus (CAN bus) and proposed alternatives, the CAN bus protocol is still the industry standard and present in most vehicles. Due to its vulnerability to potential intruders that can hinder execution or even take control of the vehicles, much work has focused on detecting intrusions on the CAN bus. However, most literature does not provide mechanisms to reason about, or respond to the attacks so that the system can continue to execute safely despite the intruder. This letter proposes a low-overhead methodology to automatically classify intrusions into predefined types once detected. Our framework: 1) groups messages of the same attacks into blocks; 2) extracts relevant features from each block; and 3) predicts the type of attack using a lightweight classifier model. The initial models depicted in this letter show an accuracy of up to 99.16% within the first 50 ms of the attack, allowing the system to quickly react to the intrusion before the malicious actor can conclude their attack. We believe this letter lays the groundwork for vehicles to have specialized runtime reactions based on the attack type.